Free Download New 70-680 Exam Dumps: PassLeader now supplying the new version of 70-680 VCE dumps, we ensure our 580q 70-680 exam questions are the most authoritative and valid compared with others’, which will ensure your 70-680 exam 100% passing, and now we are offering the free new version VCE Player along with the VCE format 580q 70-680 braindumps, also the PDF format 70-680 practice test is available now, welcome to choose.
keywords: 70-680 exam,580q 70-680 exam dumps,580q 70-680 exam questions,70-680 pdf dumps,70-680 practice test,70-680 vce dumps,70-680 study guide,70-680 braindumps,TS: Windows 7, Configuring Exam
QUESTION 381
You have a computer named Computer1 that runs Windows 7. Computer1 uses an NTFS-formatted USB drive that has ReadyBoost enabled. You need to modify the amount of space that ReadyBoost reserves on the USB drive. What should you do?
A. Open Computer and modify the properties of the USB drive.
B. Open Performance Information and Tools and run disk cleanup.
C. Open Devices and Printers and modify the properties of the USB drive.
D. Open Device Manager and modify the properties of the USB device.
Explanation:
ReadyBoostWindows 7 supports Windows ReadyBoost. This feature uses external USB flash drives as a hard disk cache to improve disk read performance. Supported external storage types include USB thumb drives, SD cards, and CF cards. Since ReadyBoost will not provide a performance gain when the primary disk is an SSD, Windows 7 disables ReadyBoost when reading from an SSD drive. External storage must meet the following requirements:
– Capacity of at least 256 MB, with at least 64 kilobytes (KB) of free space. The 4-GB limit of Windows Vista has been removed.
– At least a 2.5 MB/sec throughput for 4-KB random reads
– At least a 1.75 MB/sec throughput for 1-MB random writes
QUESTION 382
You have a computer that runs Windows Vista. You need to identify whether the computer can be upgraded to Windows 7. Which tool should you use?
A. Windows Anytime Upgrade for Windows 7
B. Windows Anytime Upgrade for Windows Vista
C. Windows 7 Upgrade Advisor
D. Windows Vista Upgrade Advisor
Answer: C
Explanation:
Windows 7 Upgrade Advisor. Prior to attempting to perform the upgrade from Windows Vista to Windows 7, you should run the Windows 7 Upgrade Advisor. The Windows 7 Upgrade Advisor is an application that you can download from Microsoft’s\ Web site that will inform you if Windows 7 supports a computer running the current hardware and software configuration of Windows Vista. Prior to running the Windows 7 Upgrade Advisor, you should ensure that all hardware that you want to use with Windows 7, such as printers, scanners, and cameras, are connected to the computer. The Upgrade Advisor generates a report that informs you of which applications and devices are known to have problems with Windows 7.
NOT Windows Anytime Upgrade. A similar compatability report is generated during the upgrade process, but the version created by the Windows 7 Upgrade Advisor is more likely to be up to date.
NOT Windows Vista Upgrade Advisor. Question specifies upgrading to Windows 7 from Windows Vista, not upgrading to Windows Vista.
QUESTION 383
You have a computer that runs Windows 7. You connect to your companys network by using a VPN connection. You discover that when you establish the VPN connection, you are unable to access Internet Web sites. When you disconnect the VPN connection, you can access Internet Web sites. You need to access Internet Web sites while you are connected to the VPN. What should you do?
A. Configure the VPN connection to use only PPTP.
B. Configure the VPN connection to use only L2TP/IPSec.
C. From the Internet Protocol Version 4 (TCP/IPv4) properties of the local area connection, disable the Automatic metric setting.
D. From the Internet Protocol Version 4 (TCP/IPv4) properties of the VPN connection, disable the Use default gateway on remote network setting.
Answer: D
Explanation:
To prevent the default route from being created In the properties of the TCP/IP protocol of the dial-up connection object, in the Advanced TCP/IP Settings dialog box, click the General tab, and then clear the Use default gateway on remote network check box.
QUESTION 384
You have a computer that runs Windows XP and a USB drive that is protected by using BitLocker To Go. You need to ensure that you can copy files from the computer to the USB drive. The solution must retain the existing files on the USB drive. What should you do?
A. From a computer that runs Windows 7, change the file system of the USB drive.
B. From a computer that runs Windows 7, disable BitLocker To Go for the USB drive.
C. Log on to Windows XP as member of the Administrators group.
D. Log on to Windows XP by using a user account that has an Encrypting File System (EFS) certificate.
Answer: B
Explanation:
BitLocker To Go does not require that the computer have a TPM chip or that Group Policy be configured to allow some other form of authentication such as a startup key. If you configure appropriate policies, devices protected by BitLocker To Go can be used in read- only mode with computers running Windows XP and Windows Vista.
QUESTION 385
You install a local printer on a computer. You share the printer. You need to ensure that only members of a local group named Group1 can print documents on the printer. Which settings should you modify on the printer?
A. Printing preferences
B. Priority
C. Security
D. Share
Answer: C
Explanation:
Restricting printer access to selected users by using security groups If you need to restrict the access of certain shared printers to a certain group of network users, do the following:
– Create a security group and then add members to the security group.
– Assign printer access permissions.
To create a security group and add member to the group:
1. Open the Windows SBS Console.
2. On the navigation bar, click the Users and Groups tab, and then click Groups.
3. In the task pane, click Add a new group. The Add a New Group Wizard appears.
In the Add a New Group Wizard, do the following:
1. On the Add a new group page, for Group type, select Security group.
2. On the Select groups members for <groupname> page, from the Users and groups list, add the network users who you want to include for the restricted printer access.
3. Follow the instructions to complete the wizard.
To assign printer access permissions:
1. Open the Windows SBS Console.
2. On the navigation bar, click the Network tab, and then click Devices.
3. From the list of printers displayed in the Printers section, click the printer that you want to view the properties for. Then in the task pane, click Printer Properties.
4. In the Printer Properties dialog box, click the Security tab, and then remove all entries in the Groups or user names list box except Administrators and Creator Owner.
5. To grant access to the printer, click Add, and then enter the names of the group or users that you want to grant access to this printer.
QUESTION 386
You have a computer that runs Windows 7. Multiple users share the computer. The computer is joined to a domain. You need to prevent the users from using more than 2 GB of disk space on drive C. What should you do?
A. From a Group Policy object (GPO), enable the Limit profile size setting.
B. Enable System Protection for Local Disk (C) and set the disk space usage.
C. Enable disk quota management on Computer1 and configure a default quota limit.
D. From a Group Policy object (GPO), enable the Limit the size of the entire roaming user profile cache setting.
Answer: C
Explanation:
Disk quotas provide administrators with a way to limit each user’s utilization of disk space on a volume. In order to set quotas, you must have Administrator rights, and the volume must be formatted with the NTFS file system. Disk quotas are based on file ownership and are independent of the folder location of the user’s files within the volume. For example, if users move their files from one folder to another on the same volume, their volume space usage does not change. However, if users copy their files to a different folder on the same volume, their volume space usage doubles. If one user creates a 200 kilobyte (KB) file, and another user takes ownership of that file, the first user’s disk use decreases by 200 KB and the second user’s disk use increases by 200 KB.
QUESTION 387
Your network contains a public computer that runs Windows 7. Multiple users log on to the computer by using a local user account named User1. Users report that they can log on to some secure Web sites by using credentials that were saved by other users. You need to prevent forms-based credentials from being saved on the computer. What should you do?
A. Remove all generic credentials from Windows Vault.
B. Remove all Windows credentials from Windows Vault.
C. Modify the Windows Internet Explorer certificates settings.
D. Modify the Windows Internet Explorer AutoComplete settings.
Answer: D
Explanation:
AutoComplete settings. AutoComplete is a feature in Internet Explorer that remembers the information you have typed into the Address bar, web forms, or password fields, and which automatically fills in that information if you start to type the same thing again later. This saves you from having to type the same information over and over.
QUESTION 388
You have two computers that run Windows 7. Both computers are connected to a network and have IP addresses within the 172.16.10.0/24 subnet. You need to ensure that both computers can join a HomeGroup. What should you do?
A. Enable network discovery.
B. Set the network location to Home network.
C. Configure Windows Firewall to allow the Netlogon service.
D. Change the IP addresses to be within the 192.168.1.0/24 subnet.
Answer: B
Explanation:
Windows Firewall does not allow you to create firewall rules for specific network locations on the basis of port address. Windows Firewall does not allow you to create rules that differentiate between the home and work network locations. You can only create rules that differentiate on the basis of home and work or public network locations.HomeGroup ConnectionsThis option decides how authentication works for connections to HomeGroup resources. If all computers in the HomeGroup have the same user name and passwords configured, you can set this option to allow Windows to manage HomeGroup connections. If different user accounts and passwords are present, you should configure the option to use user accounts and passwords to connect to other computers. This option is available only in the Home/Work network profile.
QUESTION 389
You have a computer that runs Windows 7. You need to identify how much disk space is occupied by previous versions. What should you do?
A. At a command prompt, run Diskpart.
B. At a command prompt, run Vaultcmd.
C. From System, view the System Protection settings.
D. From the properties of drive C, view the previous versions settings.
Answer: C
QUESTION 390
You have a computer named Computer1 that runs Windows 7 and Windows Internet Explorer 8. A user reports that Computer1 has a number of Internet Explorer configuration issues that cause instability when browsing the Internet. You need to configure Internet Explorer to use all default settings. What should you do from Internet Options?
A. From the Advanced tab, click Reset.
B. From the Programs tab, click Set programs.
C. From the Advanced tab, click Restore advanced settings.
D. From the Security tab, click Reset all zones to default level.
Answer: A
Explanation:
Reset Internet Explorer settings. By resetting Internet Explorer settings, you return Internet Explorer to the state it was in when it was first installed on your computer. This is useful for troubleshooting problems that might be caused by settings that were changed after installation. When you delete personal settings, some webpages that rely on previously stored cookies, form data, passwords, or previously installed browser add-ons might not work correctly. Resetting Internet Explorer to its default settings does not delete your favorites, feeds, Web Slices, and a few other personalized settings. See the table below for a complete list of all settings and information about whether they are reset or maintained. Resetting Internet Explorer’s settings is not reversible. After a reset, all previous settings are lost and cannot be recovered. Rather than resetting everything, you might want to reset specific settings or delete your webpage history. For more information, see the links at the bottom of this topic.
To reset Internet Explorer settings:
1. Close any Internet Explorer or Windows Explorer windows that are currently open.
2. Click to open Internet Explorer.
3. Click the Tools button, and then click Internet Options.
4. Click the Advanced tab, and then click Reset.
5. Select the Delete personal settings check box if you would like to remove browsing history, search providers, Accelerators, home pages, and InPrivate Filtering data.
6. In the Reset Internet Explorer Settings dialog box, click Reset.
7. When Internet Explorer finishes restoring the settings, click Close, and then click OK.
8. Close Internet Explorer.
Your changes will take effect the next time you open Internet Explorer.
http://www.passleader.com/70-680.html
QUESTION 391
You have a computer that runs Windows 7. The computer is a member of an Active Directory domain and has a shared printer. Users report that they can print to the shared printer, but they cannot delete their print jobs. You need to ensure that users can delete their own print jobs. What should you do?
A. Restart the Print Spooler service.
B. Stop sharing the local printer and then share it again.
C. Assign the Manage Documents permission to SYSTEM.
D. Assign the Manage Documents permission to CREATOR OWNER.
Answer: D
Explanation:
Manage Documents. The user can pause, resume, restart, cancel, and rearrange the order of documents submitted by all other users. The user cannot, however, send documents to the printer or control the status of the printer. By default, the Manage Documents permission is assigned to members of the Creator Owner group. When a user is assigned the Manage Documents permission, the user cannot access existing documents currently waiting to print. The permission will only apply to documents sent to the printer after the permission is assigned to the user.
QUESTION 392
You have two computers named Computer1 and Computer2 that run Windows 7. Computer1 has a dynamic disk. You remove the disk from Computer1 and connect the disk to Computer2. You need to ensure that you can open files on all hard disk drives connected to Computer2. What should you do from the Disk Management snap-in?
A. Convert a disk.
B. Rescan the disks.
C. Import a foreign disk.
D. Attach a virtual hard disk (VHD).
Answer: B
Explanation:
Moving Disks to Another Computer. Before you move disks to another computer, you should use Disk Management to make sure the status of the volumes on the disks is Healthy. If the status is not Healthy, you should repair the volumes before you move the disks. To verify the volume status, check the Status column in the Disk Management console. Your next step is to uninstall the disks you want to move. In the Computer Management Navigation pane (the left pane), open Device Manager. In the device list, double-click Disk Drives. Right-click each of the disks you want to uninstall in turn and then click Uninstall. In the Confirm Device Removal dialog box, click OK. If the disks that you want to move are dynamic disks, right-click the disks that you want to move in Disk Management, and then click Remove Disk. After you have removed dynamic disks, or if you are moving basic disks, you can disconnect the disk drives physically. If the disks are external, you can now unplug them from the computer. If they are internal, turn off the computer and then remove the disks. If the disks are external, plug them into the destination computer. If the disks are internal, make sure the computer is turned off and then install the disks in that computer. Start the destination computer and follow the instructions on the Found New Hardware dialog box. On the destination computer, open Disk Management, click Action, and then click Rescan Disks. Right-click any disk marked Foreign, click Import Foreign Disks, and then follow the on- screen instructions.
http://technet.microsoft.com/en-us/library/cc753750.aspx
QUESTION 393
You need to identify the hardware failures that have occurred on your computer in the past six months. What should you do?
A. Open Device Manager.
B. Open Reliability Monitor.
C. Create a User Defined Data Collector Set.
D. Create a new Event Trace Sessions Data Collector Set.
Answer: B
Explanation:
Reliability Monitor is an advanced tool that measures hardware and software problems and other changes to your computer. It provides a stability index that ranges from 1 (the least stable) to 10 (the most stable). You can use the index to help evaluate the reliability of your computer. Any change you make to your computer or problem that occurs on your computer affects the stability index. The Reliability Monitor is intended for advanced computer users, such as software developers and network administrators.
Click to open Action Center.
Click Maintenance. Then, under Check for solutions to problem reports, click View reliability history.
In Reliability Monitor, you can:
Click any event on the graph to view its details.
Click Days or Weeks to view the stability index over a specific period of time. Click items in the Action column to view more information about each event. Click View all problem reports to view only the problems that have occurred on your computer. This view doesn’t include the other computer events that show up in Reliability Monitor, such as events about software installation.
QUESTION 394
You have a computer named Computer1 that runs Windows 7. You need to configure Computer1 to support the collection of Windows system events from other computers. Which command should you run?
A. Wecutil qc
B. Winrm quickconfig
C. Winrs /r:Computer1
D. Wmic /aggregate
Answer: A
Explanation:
Wecutil To configure a computer running Windows 7 to collect events, open an elevated command prompt and enter the following command to configure the Windows Event Collector service: wecutil qc{qc | quick-config}Configures the Windows Event Collector service to ensure a subscription can be created and sustained through reboots. This includes the following steps:
*. Enable the ForwardedEvents channel if it is disabled.
*. Set the Windows Event Collector service to delay start.
*. Start the Windows Event Collector service if it is not running.
QUESTION 395
You have a netbook computer that runs Windows 7. The computer has a single 30 GB partition that has 10 GB of free space. You need to create a system image of the computer by using Windows Backup. You must achieve this goal by using the minimum amount of time. What should you do first?
A. Attach an external hard disk.
B. Attach an external DVD burner.
C. Convert the local hard disk to a GPT disk.
D. Create and attach a virtual hard drive (VHD).
Answer: A
Explanation:
Scheduling Backups with the Backup And Restore Console Windows 7 Backup uses shadow copies to take a snapshot of your files, allowing the backup to completely back up files even if they are open. Backups are configured and scheduled by using the Backup And Restore console under System And Security in Control Panel. You can select the following types of backup destination: An external hard driveExternal hard drives are more expensive to purchase than internal hard drives, although you need to balance this against the cost of fitting the internal drive. They can be removed and stored in a secure location. However, they are typically slower than internal hard drives and tend to be less reliable, mainly because they are by default formatted using FAT rather than NTFS. You cannot use an external hard drive for a System Image backup unless you convert its filing system to NTFS. Because it is easily removable, it is more likely that an external hard drive will be missing when a scheduled backup is required.
QUESTION 396
A company has client computers that run Windows 7. You need to secure a virtual private network (VPN) connection on the client computers so that two-factor authentication is used. Which setting should you choose? (To answer, select the appropriate setting in the work area.)
Answer: 
QUESTION 397
You have a portable computer that runs Windows 7. Windows Backup is configured to run every day at 15:00. You need to prevent backups from automatically running when the computer is running on the battery. What should you do?
A. From Backup and Restore, click Change settings.
B. From Task Scheduler, modify the Automatic Backup task.
C. From Power Options, modify the settings of the current power plan.
D. From the local computer policy, modify the power management settings.
Answer: B
Explanation:
To set power management options for a scheduled task
– Open Task Scheduler.
– Right-click the task for which you want to set power management options, and then click Properties.
– On the Settings tab, under Power Management, do one or more of the following:
– To conserve the battery power of your computer, select the Don’t start the task if the computer is running on batteries check box.
– To stop the task if the computer starts running on battery power, select the Stop the task if battery mode begins check box.
– To wake your computer from hibernation or standby to run a task, select the Wake the computer to run this task check box.
Task Scheduler. With Scheduled Tasks, you can schedule any script, program, or document to run at a time that is most convenient for you. Scheduled Tasks starts every time that you start Windows and runs in the background, and it starts each task that you schedule at the time that you specify when you create the task.
QUESTION 398
A company has client computers that run Windows 7. You set up a virtual private network (VPN) infrastructure that uses a preshared key for authentication. You need to create the VPN connection on the client computers. Which setting should you choose? (To answer, select the appropriate setting in the work area.)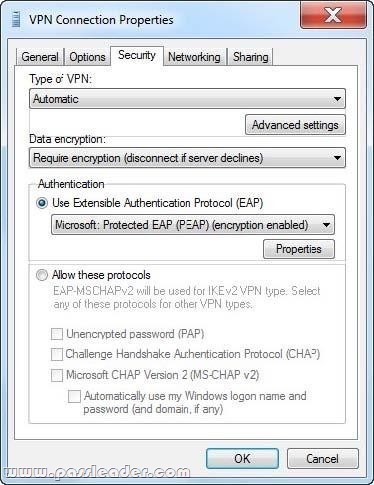
Answer: 
QUESTION 399
Note: This question is part of a series of questions that use the same set of answer choices. An answer choice may be correct for more than one question in the series.
A Remote Assistance session is established with a user’s computer that runs Windows 7 Enterprise. You need to verify that a local file is encrypted with the Encrypting File System (EFS). What should you use to accomplish this goal?
A. The Netsh command
B. The Folder Properties window
C. Device Manager
D. Share permissions
E. The Services Management console
F. The Group Policy Management console
G. The Icacls command
H. The User Account Control Settings Control Panel window
I. Local Users and Groups
Answer: B
Explanation:
Right-click the file or folder, Select Properties, Click the Advanced button under the Attributes section If Check the box next to “Encrypt contents to secure data” is checked, then the file is encrypted using EFS.
QUESTION 400
A user-installed Windows update for Windows 7 has caused an error in software that is critical to the user. You need to find and uninstall the update to restore functionality to the software. Which settings categories should you choose? (To answer, select the appropriate settings in the work area.)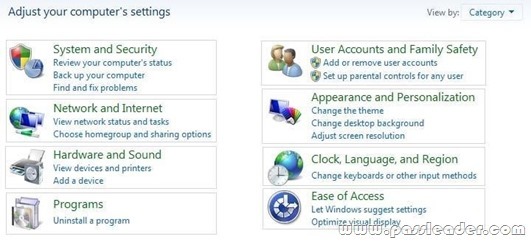
Answer: